
![]()
A brand new Android adware has surfaced that disguises itself as a system element and may entry quite a lot of smartphone capabilities together with the microphone and digicam to secretly document the consumer.
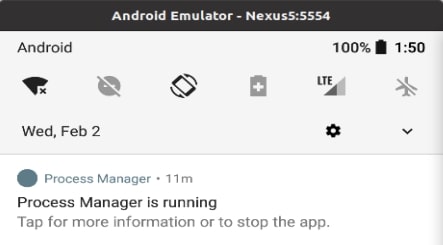
Researchers from Lab52 found the malicious APK adware that’s named “Course of Supervisor” and may add info gleaned from units it’s put in on to a 3rd social gathering. It’s nonetheless not clear how the adware is distributed however as soon as put in, it makes an attempt to cover by utilizing a gear-shaped icon and posing as a respectable Android system element, Bleeping Laptop reviews.

As soon as the applying is run, a warning will seem that asks the consumer to grant permission to the applying, which incorporates display unlock makes an attempt, locking the display, setting the system world proxy, setting the display lock password expiration, setting storage encryption, and disabling cameras. Lab52 discovered numerous permissions that it requests together with:
- GPS knowledge together with telephone location
- Community standing
- WiFi info
- Full entry to the digicam for each picture and video seize
- Audio modifications
- Entry to name logs
- Entry to contact record
- The flexibility to learn exterior storage
- The flexibility to put in writing to a reminiscence card
- SMS entry on the SIM card
- Entry to the audio recorder
- Permission to ship SMS messages
- Permission to forestall a decice from locking or hibernating
After it has been chosen and runs, the icon disappears and the malicious utility continues to run within the background. Oddly, it exhibits as lively within the notification bar. Clearly, this lengthy record of permission can be an enormous privateness breach for the consumer, however the existence of the everlasting notification is complicated, as adware like this is able to profit from being fully hidden from the consumer.
Regardless of the case, the knowledge that’s collected from contaminated units is shipped within the JSON format to a command and management server with an IP deal with in Russia. Bleeping Laptop says that the best way this adware works is just like strategies utilized by Russian state-supported hacking group Turla, however stopped in need of making a definitive hyperlink on this case. If Turla is concerned, the app could also be propagating via quite a lot of social engineering methods or phishing.
Lab52 discovered a hyperlink to a Google Play retailer itemizing known as “Roz Dhan: Earn Pockets money,” which makes use of a referral system to earn cash. The attacker appears to put in the app on the goal system and make a revenue.
Android customers are inspired to have a look at app permissions they’ve granted and examine for the “Course of Supervisor” utility and revoke entry if it seems.
Picture credit: Header picture licensed through Depositphotos.




